Cybersecurity safeguards our digital presence from cyber threats; it encompasses the practices and measures taken to protect computer systems, networks, and data from unauthorized access, damage, or theft. In our increasingly interconnected world, the importance of cybersecurity has never been more evident.
By implementing robust cybersecurity measures, individuals and organizations can mitigate the risks posed by cybercriminals and protect sensitive information. The threat landscape constantly evolves from personal data breaches to large-scale corporate cyberattacks.
Importance of Cybersecurity
Cybersecurity is essential in today’s digital world. The ever-expanding digital landscape has provided immense communication, collaboration, and innovation opportunities. However, it has also exposed individuals and organizations to various cyber threats. Cybersecurity breaches can lead to significant repercussions, such as financial losses, reputational damage, and compromised personal or business information.
By prioritizing cybersecurity, individuals and organizations can:
- Safeguard Sensitive Information: Cybersecurity measures protect sensitive data, such as personal information, financial records, and intellectual property, from falling into the wrong hands.
- Ensure Business Continuity: A cyber attack can disrupt operations, leading to significant financial losses. Robust cybersecurity measures help maintain business continuity and minimize downtime.
- Maintain Customer Trust: Customers entrust businesses with their personal information. Organizations prioritizing cybersecurity demonstrate their commitment to protecting customer data and fostering trust and loyalty.
- Adhere to Regulatory Compliance: Many industries have specific regulations and compliance requirements regarding data protection. Implementing cybersecurity measures ensures adherence to these regulations and avoids legal consequences.
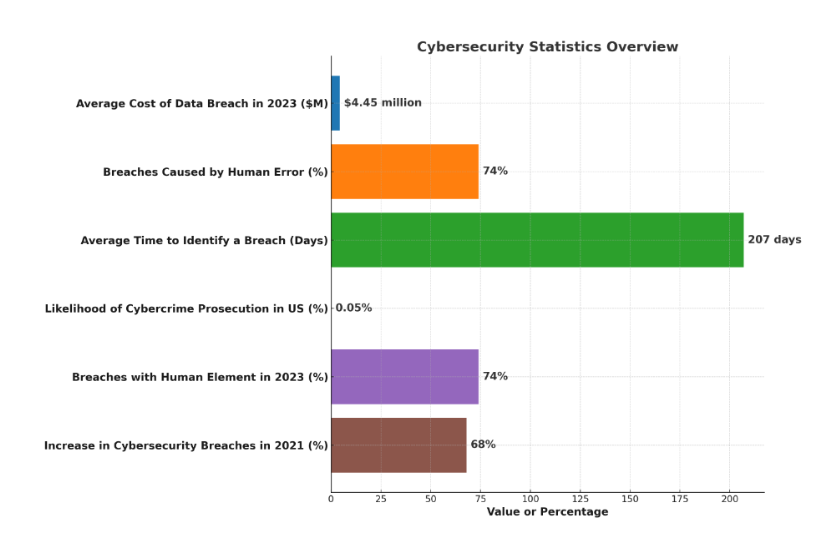
According to a report by Varonis, here are some of the most important cybersecurity statistics and trends for 2023
Protective Measures
It’s crucial to employ various protective measures to safeguard your digital presence. Let’s explore three fundamental measures: firewalls, encryption, and strong passwords.
Firewalls
Firewalls act as a protective barrier, shielding your computer or network from potential internet threats. They analyze incoming and outgoing network traffic, allowing or blocking specific connections based on predefined security rules. Firewalls are vital in preventing unauthorized access to systems and thwarting malicious activities.
Encryption
Encryption is the process of converting information into an unreadable format, known as ciphertext, to protect it from unauthorized access. It guarantees that in case of interception, the data will remain incomprehensible to unauthorized individuals. Encryption is crucial in securing sensitive data, such as financial transactions and personal information.
Strong Passwords
Passwords serve as the initial defense against unauthorized access to accounts and systems. To enhance security, it is crucial to generate strong and distinctive passwords that are difficult to guess. A strong password should consist of a combination of uppercase and lowercase letters, numbers, and special characters.
Furthermore, regularly updating passwords and utilizing multi-factor authentication provides an additional layer of protection.
Types of Cyber Threats
Gaining a clear understanding of the various types of cyber threats is essential for effectively combating them. Let’s explore three common types: malware, phishing, and social engineering.
Malware
Malware refers to malicious software designed with the explicit purpose of causing harm or exploiting vulnerabilities in computer systems or networks. It includes viruses, worms, Trojans, ransomware, and spyware. Malware can compromise the security of your digital presence, leading to data breaches, financial losses, and unauthorized access.
Phishing
Phishing is a manipulative tactic employed by cybercriminals to trick individuals into divulging confidential information, including passwords and credit card details. Phishing attacks often occur via email, where the attacker impersonates a trustworthy entity to trick the recipient into taking action. Recognizing and avoiding phishing attacks is crucial to maintaining cybersecurity.
Social Engineering
Social engineering involves manipulating individuals to gain access to confidential information. Cybercriminals exploit human psychology and trust to deceive people into revealing sensitive information or performing actions compromising security.
Social engineering techniques include pretexting, baiting, and tailgating. By familiarizing themselves with these techniques and maintaining a vigilant attitude, individuals can effectively shield themselves against social engineering attacks.
Evolving Cyber Threat Landscape
The cyber threat landscape is constantly evolving, and it’s essential to stay updated to counter emerging threats effectively. Let’s explore the concept of emerging threats and cybersecurity best practices.
Emerging Threats
As technology advances, new cyber threats continue to emerge. It’s crucial to be aware of these threats to mitigate the risks they pose. Some examples of emerging threats include zero-day exploits, artificial intelligence-based attacks, and IoT (Internet of Things) vulnerabilities. Individuals and organizations can proactively implement preventive measures by staying informed about emerging threats.
Cybersecurity Best Practices
Maintaining strong cybersecurity defenses requires adopting best practices. Here are some practical tips that can bolster your cybersecurity defenses:
- Regularly Update Software: Ensure the safety of your systems by regularly updating your operating systems, applications, and antivirus software to guard against known vulnerabilities.
- Implement Strong Authentication: Use multi-factor authentication whenever possible to add an extra layer of security to your accounts.
- Educate and Train Users: Raise awareness about cybersecurity among employees, family members, and friends. Provide training on recognizing and avoiding common threats.
- Back-Up Your Data: Regularly back up essential data to ensure quick recovery in case of a cyber-attack or system failure.
- Use Secure Networks: When accessing sensitive information or conducting financial transactions, use secure networks such as virtual private networks (VPNs) or trusted Wi-Fi networks.
- Be Cautious of Suspicious Emails and Links: It is important to avoid clicking on any links that appear suspicious or downloading attachments from unknown sources. Verify the sender’s authenticity before providing any sensitive information.
- Regularly Monitor Accounts: Monitor your financial accounts, credit reports, and online activities for any signs of unauthorized access or suspicious activity.
- Secure Your Mobile Devices: Implement strong passcodes or biometric authentication on your mobile devices and enable remote tracking and data wiping in case of loss or theft.
By adhering to these Best Practices, you can greatly diminish the chances of becoming a target of cyber threats.
Conclusion
In an increasingly interconnected and digitized world, prioritizing cybersecurity is paramount. You can proactively protect your digital presence by defining cybersecurity and understanding its significance. Protective measures like firewalls, encryption, and strong passwords fortify your defenses against cyber threats.
Moreover, familiarizing yourself with different types of cyber threats, such as malware, phishing, and social engineering, empowers you to recognize and combat them effectively. Stay updated with the evolving cyber threat landscape, including emerging threats, and adopt cybersecurity best practices to maintain robust defenses.
Remember, cybersecurity is a continuous effort. By making it a priority and staying informed, you can confidently safeguard your digital world and navigate the digital landscape.

