In today’s digital age, businesses heavily rely on technology and interconnected networks, so safeguarding digital infrastructure cannot be overstated. As companies adopt digital transformation, they need to deal with the potential risks that come along with it.
The security and integrity of digital systems are at risk due to the increasing frequency and sophistication of cyber threats. Conducting a thorough risk assessment and implementing preventive measures is paramount to mitigate these risks.
The Need for Risk Assessment
Performing a thorough evaluation to identify potential risks is the initial action you should take to protect your digital infrastructure. This process involves identifying potential vulnerabilities and evaluating the likelihood and impact of various risks. By thoroughly assessing risks, organizations gain valuable insights into their existing security posture and can make informed decisions to enhance their defenses.
A risk assessment helps organizations understand the potential consequences of security breaches, such as unauthorized access to sensitive data, financial losses, reputational damage, or disruption of critical operations. It enables proactive planning by identifying areas of vulnerability and prioritizing resources to address them effectively.
Identifying Vulnerabilities in Your Digital Infrastructure
Digital infrastructure encompasses various components, including networks, systems, applications, and data repositories. Each of these elements can be vulnerable to different types of risks. It is crucial to examine them individually to identify potential weaknesses and develop appropriate countermeasures.
For instance, network infrastructure vulnerabilities may include outdated firmware, misconfigured firewalls, or unpatched software. Identifying and addressing these weaknesses can significantly bolster your network security. Similarly, system vulnerabilities may arise from inadequate access controls, unpatched operating systems, or insecure configurations. Regular audits and assessments of these systems are essential to maintain a robust security posture.
Implementing Cybersecurity Best Practices
Mitigating risks requires the implementation of cybersecurity best practices throughout an organization. These measures include various strategies aimed at safeguarding digital infrastructure against potential threats. Here are some key areas to focus on:
Employee Training and Cybersecurity Awareness
The security of digital systems relies heavily on the involvement of employees. According to recent reports, cyberattacks will cost businesses an average of $4.35 million, and the number of yearly reported cyberattacks is rising in almost every country. Therefore, It is crucial to provide cybersecurity training to employees and raise awareness about the potential risks they may face.
Regular training programs can educate employees about identifying phishing attempts, using strong passwords, and following proper security protocols. Organizations can minimize the risk of security incidents caused by human errors by promoting a cybersecurity awareness culture.
Securing Network Infrastructure
Network infrastructure serves as the backbone of digital operations, making it an attractive target for cybercriminals. To secure network infrastructure effectively, organizations should implement measures such as:
- Using strong encryption protocols to protect data in transit.
- Segmenting networks to limit the impact of a potential breach.
- Implementing robust access controls and authentication mechanisms.
- Regularly monitoring network traffic for anomalies and suspicious activities.
Protecting Data and Privacy
Data protection and privacy are paramount in today’s regulatory landscape and consumer expectations. Organizations must implement measures to protect sensitive data and comply with data protection regulations. Some essential steps include:
- Sensitive data should be encrypted at rest and in transit.
- Access controls should be in place to limit data exposure.
- Regular data backups should be conducted to prevent loss or unauthorized access.
- Privacy impact assessments should be performed to identify and address privacy risks.
Regularly Updating and Testing Cybersecurity Measures
Cyber threats evolve rapidly, requiring organizations to stay vigilant and adapt their security measures accordingly. Regularly updating and testing cybersecurity measures is vital to ensure their continued effectiveness. Some essential practices in this regard include:
Importance of Patch Management
Cybercriminals commonly exploit software vulnerabilities. Regularly applying security patches and updates is extremely important to address any vulnerabilities that may exist. Organizations must establish and maintain robust processes for patch management to ensure all systems and applications are up to date.
Conducting Security Audits and Penetration Testing
Security audits and penetration testing are proactive measures to identify vulnerabilities in digital infrastructure. Conducting regular audits and engaging ethical hackers to perform penetration testing can help uncover potential weaknesses before malicious actors exploit them. These assessments offer valuable insights into an organization’s security controls’ effectiveness, aiding in informed decision-making for improvements.
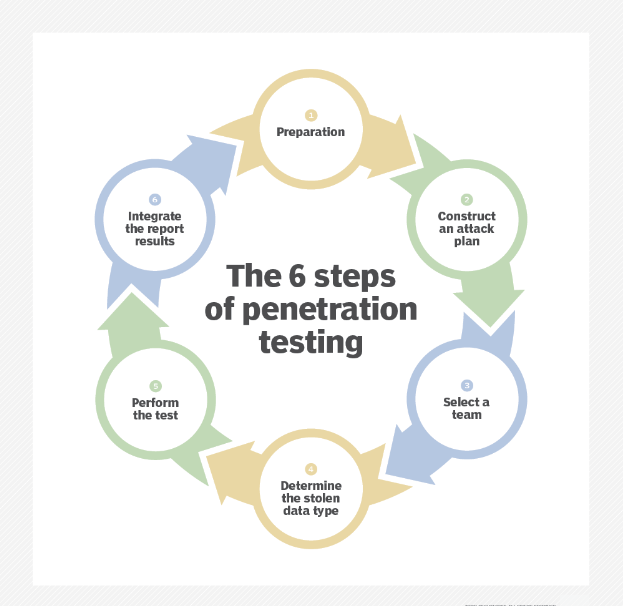
Penetration testing is an important part of network security, but it is not enough to fully assess the vulnerabilities of a system. On the other hand, a vulnerability assessment is a distinct process that aims to identify weaknesses in a network and recommend appropriate measures for mitigating or eliminating risks.
Monitoring and Incident Response
A comprehensive monitoring system and an effective incident response plan are essential in promptly detecting and responding to cybersecurity incidents. It is important to deploy monitoring tools to detect and alert suspicious activities and to have incident response protocols in place to outline the steps to be taken in the event of a security breach. Regularly reviewing and testing these monitoring and response mechanisms is crucial to ensure their efficacy.
Conclusion
Safeguarding digital infrastructure is an ongoing process that requires a proactive approach. Organizations must take vital steps to conduct a risk assessment to identify vulnerabilities, implement cybersecurity best practices, regularly update and test security measures, and foster a culture of cybersecurity awareness. Prioritizing risk prevention and assessment can protect businesses’ digital assets, maintain customer trust, and ensure operational continuity.
FAQs
Why is employee training and cybersecurity awareness important?
Employee training and cybersecurity awareness are critical because human errors can result in security incidents. Educating employees about potential risks, including phishing attempts, and promoting a cybersecurity awareness culture can help organizations minimize the risk of security breaches caused by human mistakes.
What are the benefits of prioritizing risk prevention and assessment?
Prioritizing risk prevention and assessment is crucial to safeguarding digital assets, maintaining customer trust, and ensuring operational continuity. By proactively addressing vulnerabilities and implementing appropriate measures, organizations can mitigate risks and minimize the potential impact of security breaches.

